
MCMC Blocks Vercel App Domains — A Misguided Approach to Web Filtering?
If you’ve been in the developer space for a while, you might recall a controversial move by Malaysia’s MCMC (Malaysian Communications and Multimedia Commission) some time ago — when they blocked...

Reflecting on Ren Zhengfei’s Huawei Interview: Science, Innovation, and China’s Path Forward
In a recent face-to-face dialogue at Huawei’s headquarters in Shenzhen, People’s Daily reporters Hu Jian and Chen Jiaxing sat down with Huawei founder and CEO Ren Zhengfei to discuss key topics of...

iOS 26: The Dawn of a New Era for Apple's Operating Systems
The air is thick with anticipation as we approach WWDC 2025, and this year, it feels different. Apple isn't just delivering incremental updates; they're heralding a significant shift. Gone are the fam...
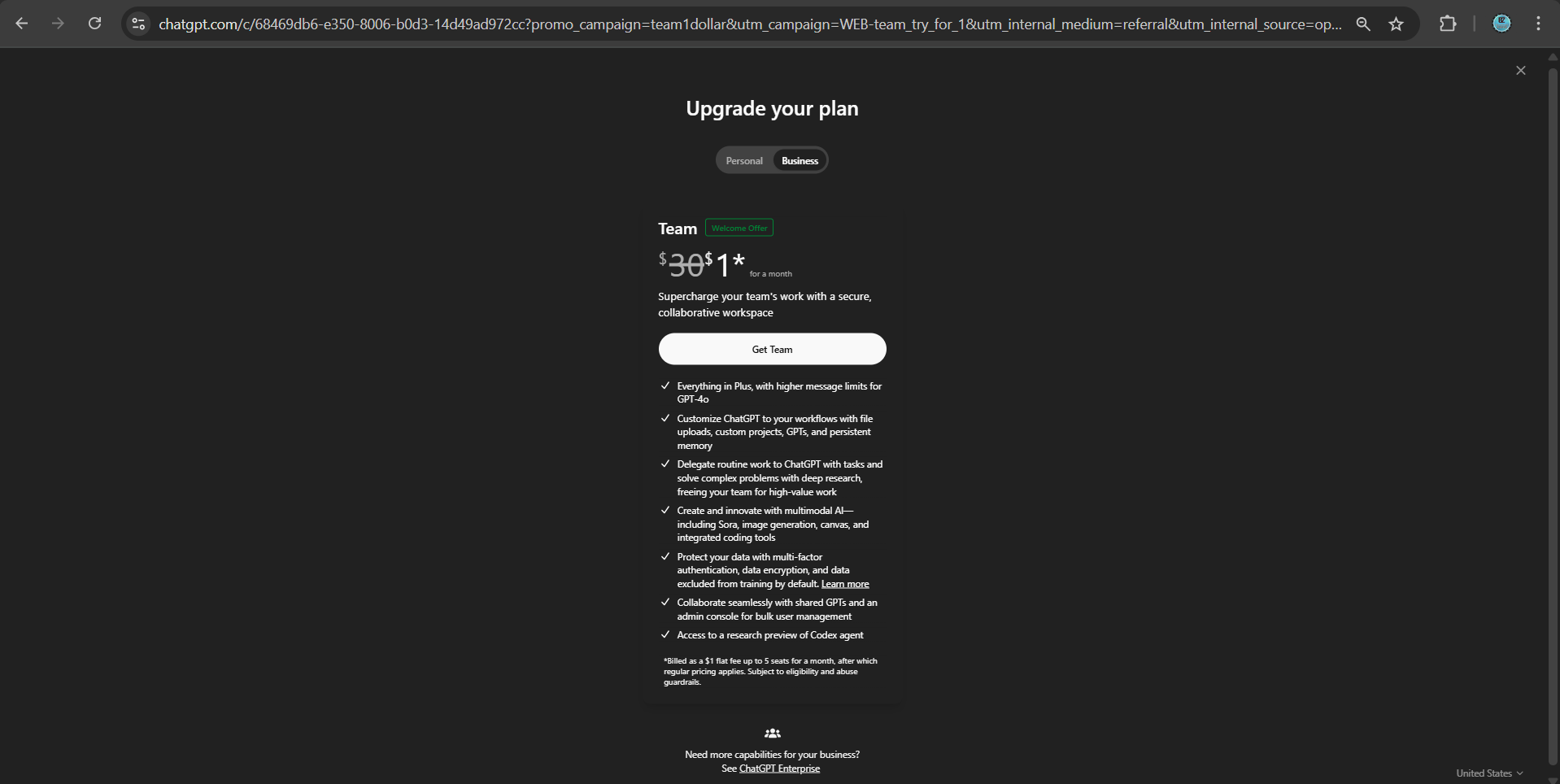
ChatGPT Team Plan Now Just $1 – Includes Access for 5 Members
Here’s how you can experience and use the ChatGPT Team Plan for just $1 — a limited-time offer that gives you access to enhanced features and greater value. While the process of upgrading and subs...
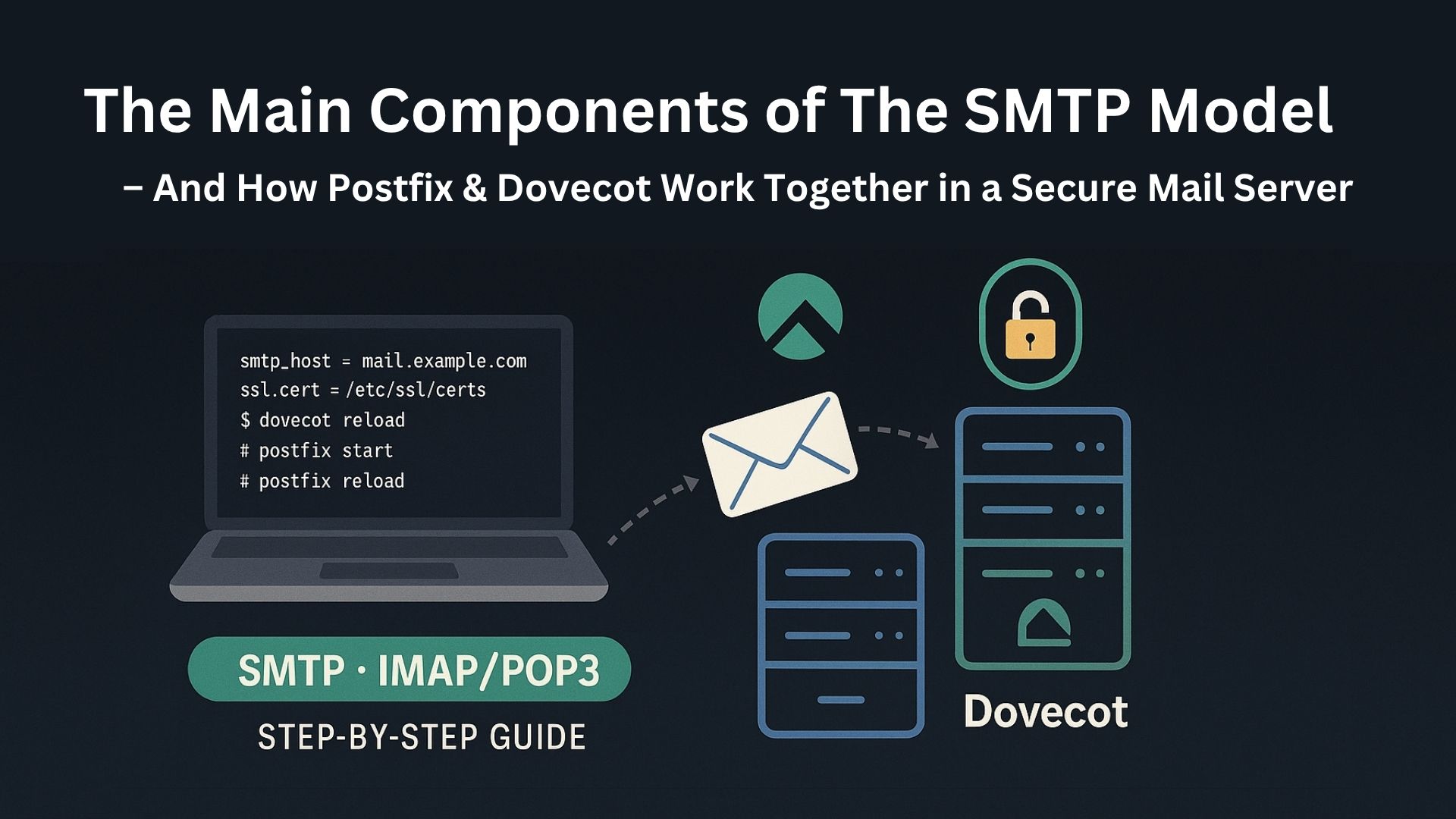
Understanding the Main Components of the SMTP Model – And How Postfix & Dovecot Work Together in a Secure Mail Server
Email is one of the oldest and most essential forms of digital communication. Behind every email sent, there's a well-orchestrated set of systems and protocols working in harmony. One of the core prot...

APU Sustainable Future Fusion (APU SFF): Empowering Students to Build a Greener, Smarter, and More Inclusive Future
APU Sustainable Future Fusion (APU SFF) is a leading student-led sustainability club at the Asia Pacific University of Technology and Innovation (APU), Malaysia, committed to creating a meaningful imp...

Asia Pacific University (APU) Celebrates World Diversity Day 2025 with a Grand Cultural Showcase
Asia Pacific University of Technology & Innovation (APU) came alive in celebration of World Diversity Day 2025, a vibrant cultural extravaganza organised by Sustainable Future Fusion (SFF) in coll...

The World Cultural Diversity Forum 2025: Championing Culture for a Sustainable Future
As President of Sustainable Future Fusion (SFF@APU), I, Khoo Lay Yang 邱励扬, had the honour of representing Asia Pacific University of Technology & Innovation (APU) at the World Cultural Diver...
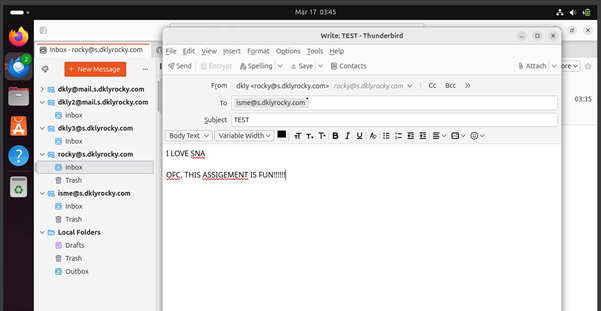
Secure Email Server Deployment with Postfix and Dovecot on Rocky Linux Using VirtualBox
This project focuses on the deployment of a secure and fully functional email server using Rocky Linux within a VirtualBox environment. Acting as the system administrator, I am responsible for setting...

Vulnerability Report: Unauthenticated RTMP Push & Public Playback on Kuaishou (快手短视频)
A critical vulnerability has been discovered in the Kuaishou streaming infrastructure that allows unauthenticated live streaming via RTMP to arbitrary stream keys. Once pushed, these streams are publi...
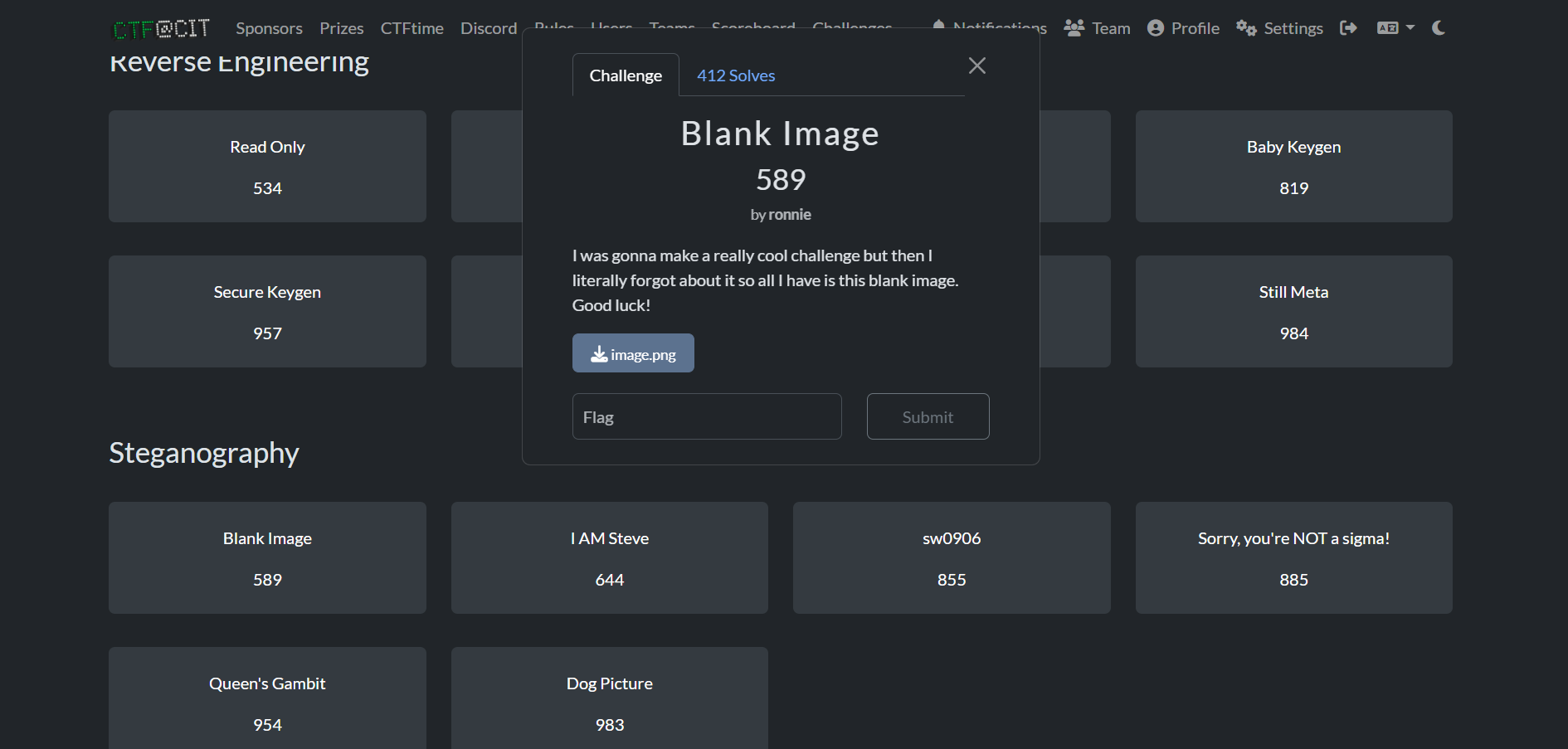
CTF@CIT 2025 Write-Up: Blank Image (Steganography)
In the CTF@CIT 2025 cybersecurity competition, I participated in the Steganography category and came across an interesting challenge named "Blank Image". Despite appearing as a blank image, a clue in ...

CTF@CIT 2025 Write-up: Breaking Authentication via SQL Injection
In this challenge, we are presented with a seemingly innocent login form and a mysterious prompt: "Say my username." While it appears simple on the surface, this challenge requires a solid understandi...
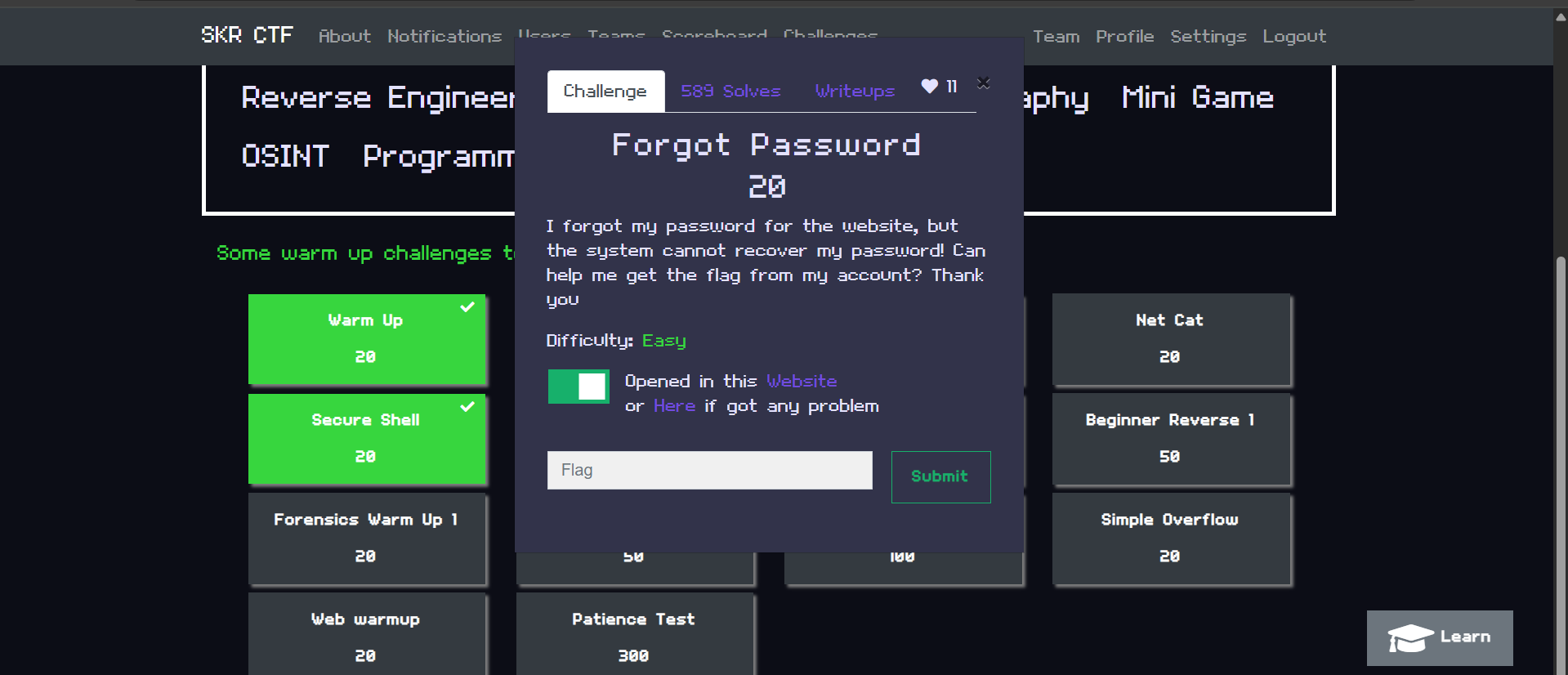
SKRCTF - Forgot Password Challenge: Exploiting Client-Side Authentication
The "Forgot Password" challenge from SKRCTF highlights a classic web security flaw commonly seen in beginner-level Capture The Flag (CTF) competitions. The challenge presents a simple login page where...
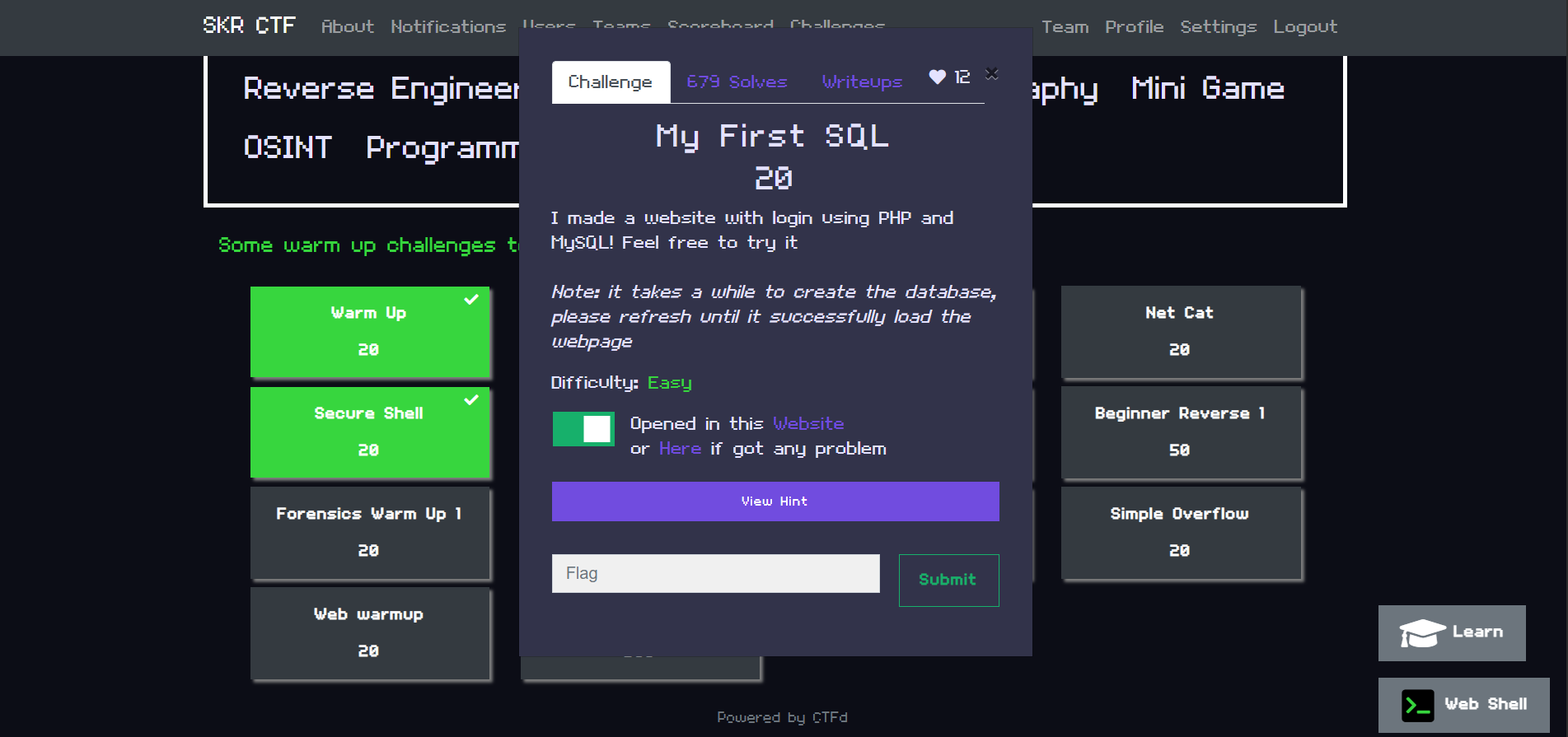
SKRCTF: My First SQL – Beginner SQL Injection Challenge Writeup
The "My First SQL" challenge from the SKRCTF series offers an accessible introduction to SQL injection (SQLi) vulnerabilities, making it an excellent starting point for individuals new to web security...
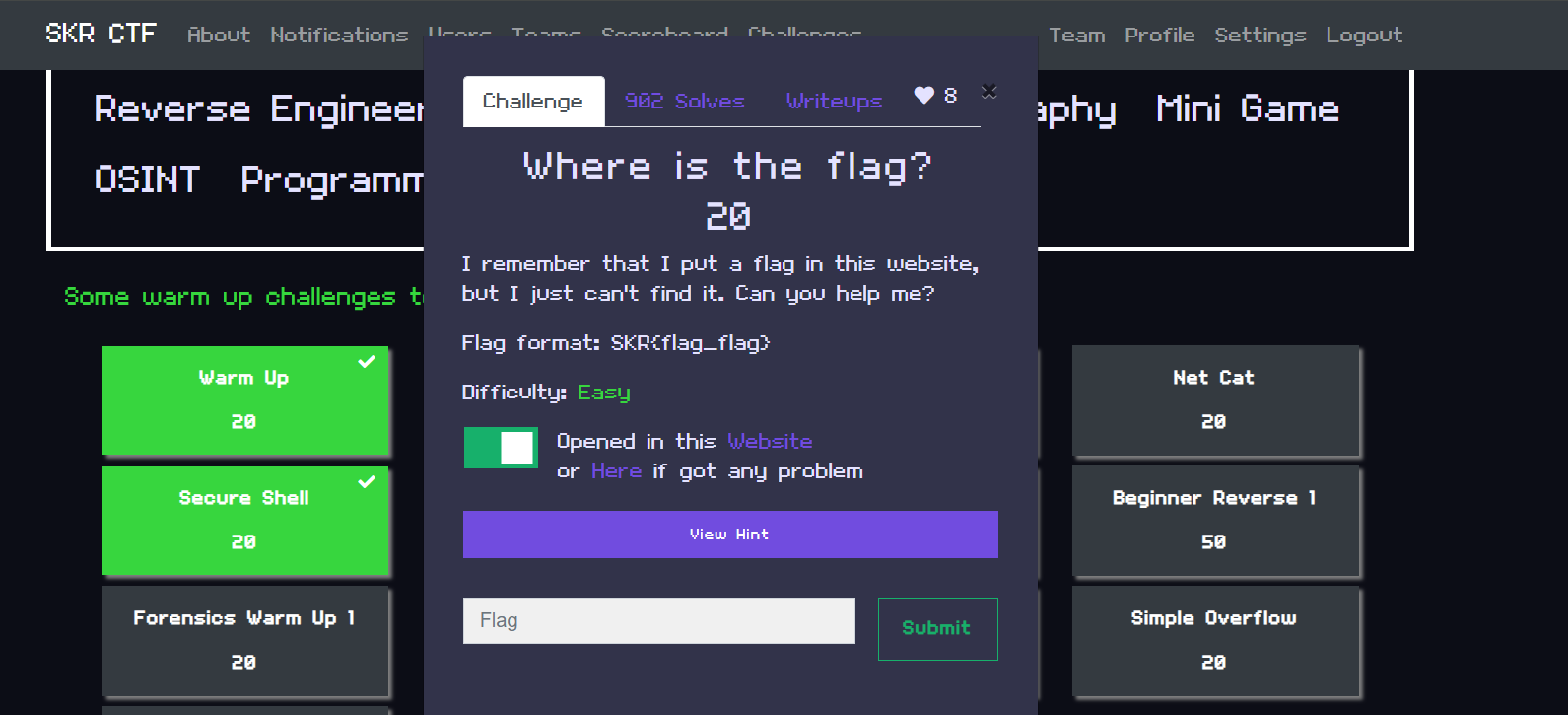
SKRCTF: Where is the Flag? – Web CTF Challenge Writeup
The "Where is the flag?" challenge from the SKRCTF series is a beginner-friendly web challenge that emphasises the importance of thorough inspection and attention to detail in web security.Challenge O...
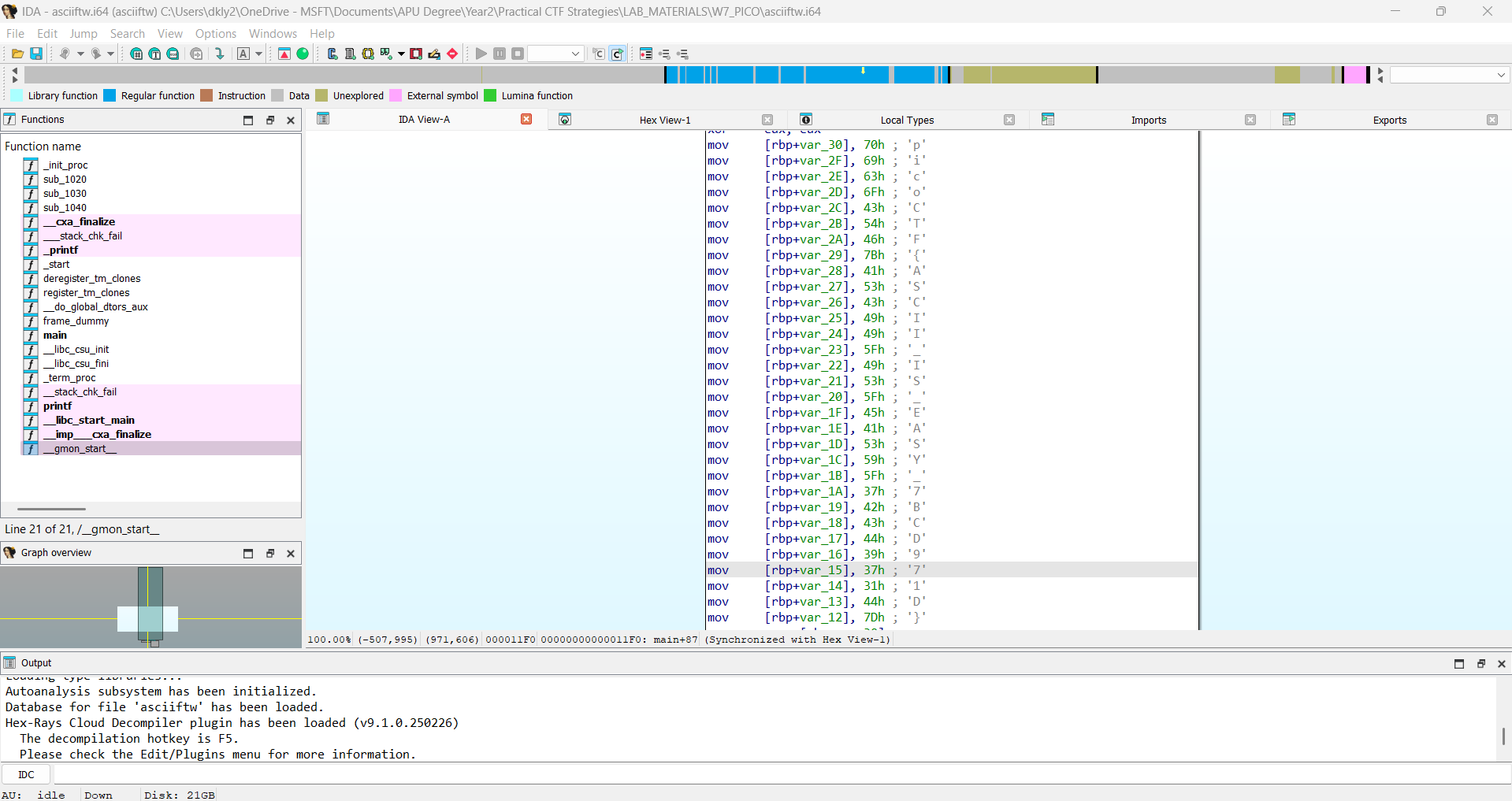
Reverse Engineering in picoCTF: A Journey Through Binaries, Bits, and Flags
Reverse engineering is a core skill in cybersecurity that involves analyzing a system, software, or binary to understand its design, functionality, or hidden components, often without access to its so...

A Rewarding Journey: Collaborating with PKKTB and SISA for Sustainable Futures
As the President of Sustainable Future Fusion (SFF) at Asia Pacific University of Technology & Innovation (APU), I am honoured to reflect on one of the most significant milestones of our journey s...

Forging New Horizons: Pioneering the APU x KLTESA Alliance for a Sustainable Future
On 21 November 2024, a significant milestone was achieved as the Asia Pacific University of Technology & Innovation (APU) and the Kuala Lumpur Tourism, Entrepreneurs, Stakeholders Association (KLT...
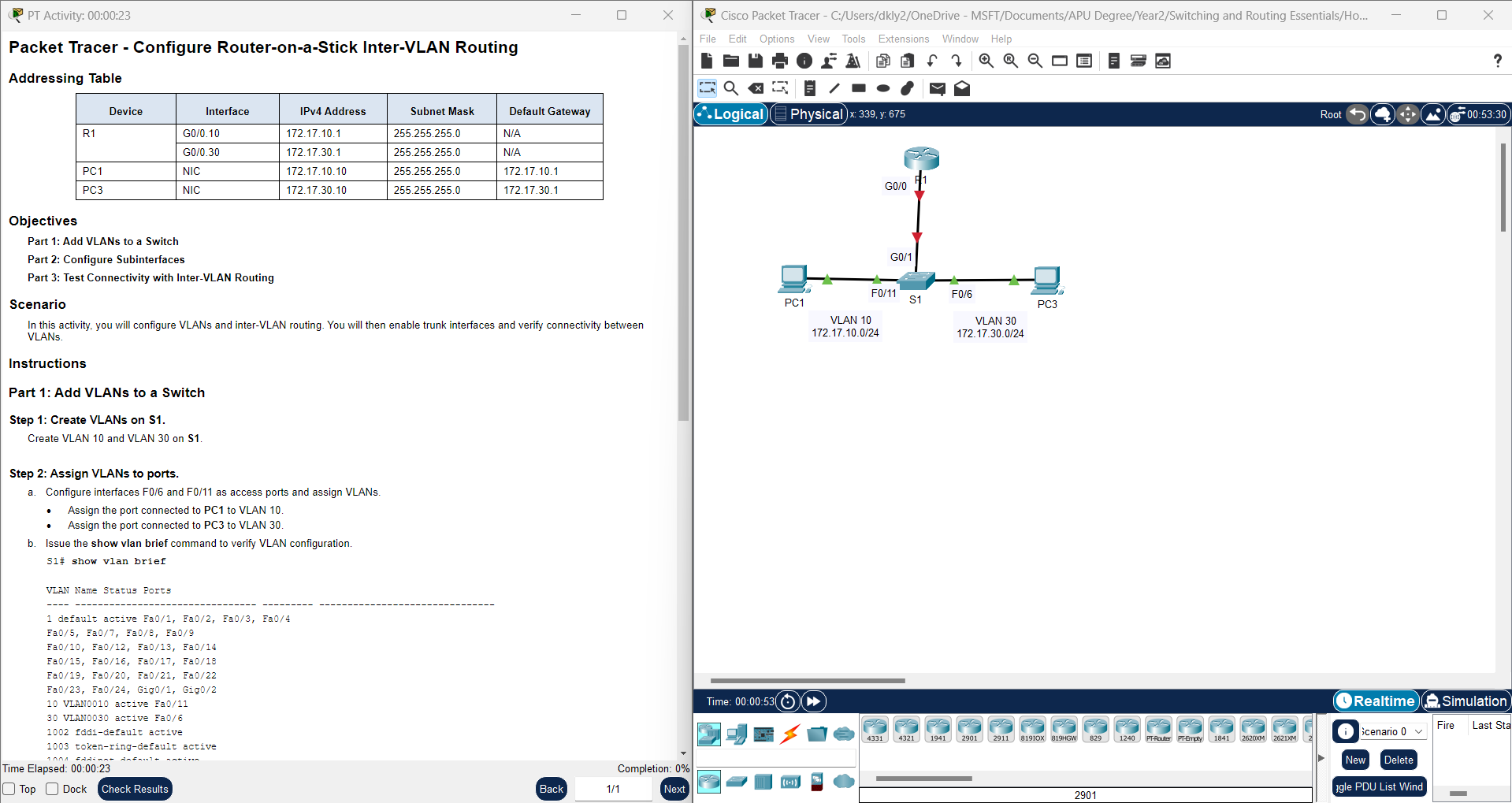
4.2.7 Packet Tracer - Configure Router-on-a-Stick Inter-VLAN Routing
In this lab, we will configure Router-on-a-Stick for Inter-VLAN Routing using Packet Tracer. Router-on-a-Stick is a networking technique used to allow communication between devices in different VLANs....
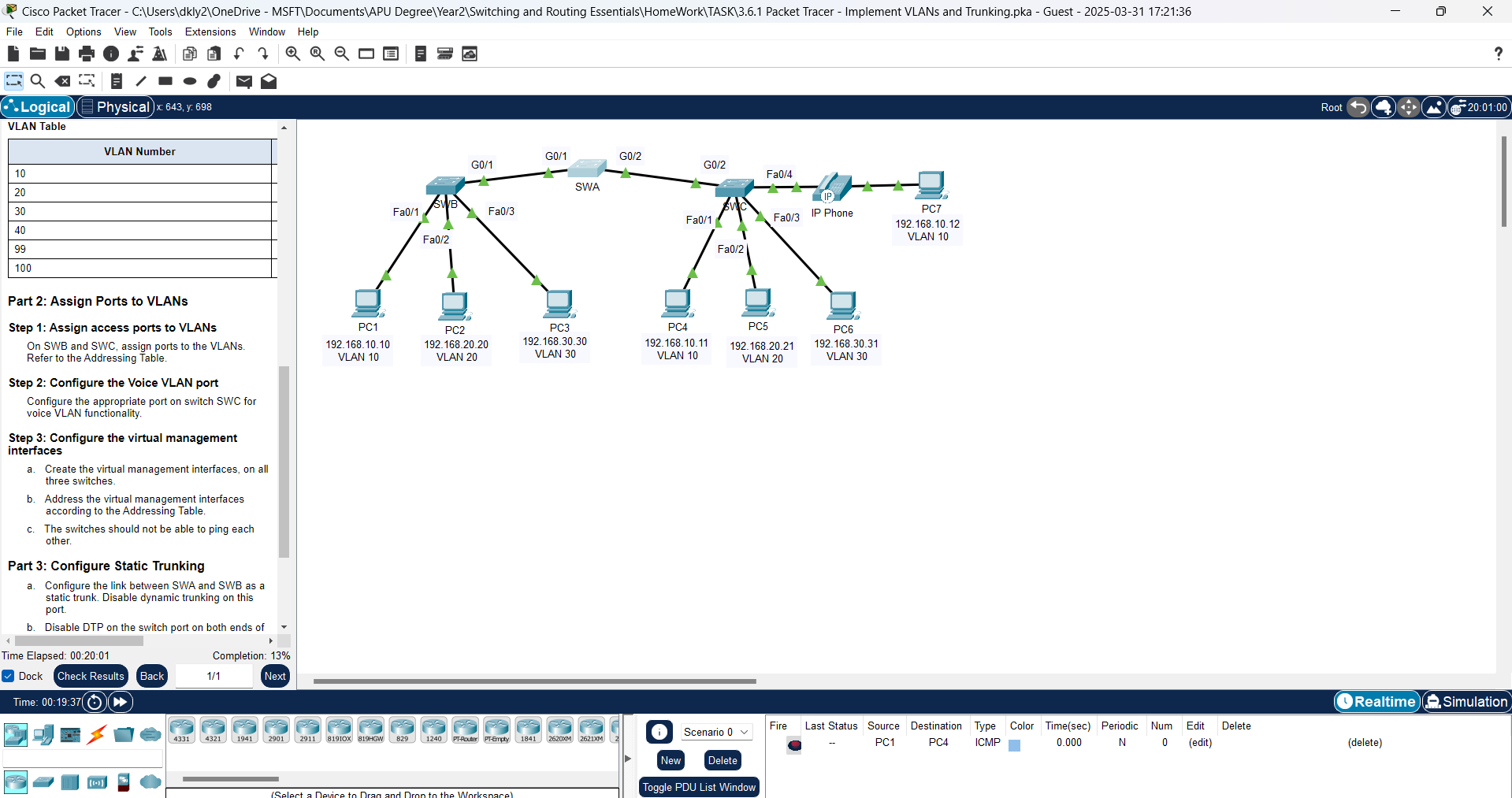
3.6.1 Packet Tracer - Implement VLANs and Trunking | Cisco Networking
In modern networking, Virtual Local Area Networks (VLANs) and trunking play a crucial role in segmenting networks and ensuring efficient communication between different departments or devices. VLANs a...