The "Forgot Password" challenge from SKRCTF highlights a classic web security flaw commonly seen in beginner-level Capture The Flag (CTF) competitions. The challenge presents a simple login page where the password recovery mechanism is either broken or nonexistent, prompting users to find another way in. By inspecting the client-side JavaScript code, we uncover hardcoded credentials, revealing how insecure it is to handle authentication logic on the frontend. This challenge teaches an important lesson about proper authentication practices and reinforces the importance of never trusting the client side with sensitive logic.
Challenge Overview
Descriptions: I forgot my password for the website, but the system cannot recover my password! Can help me get the flag from my account? Thank you
Difficulty: Easy
Challenge Link: https://skrctf.me/challenges#Forgot%20Password
Solutions
Step 1: I opened the site and was greeted with a basic login form asking for a username and password.
Step 2: After a few trial logins (which all returned Wrong Creds!), I opened the browser’s developer tools.
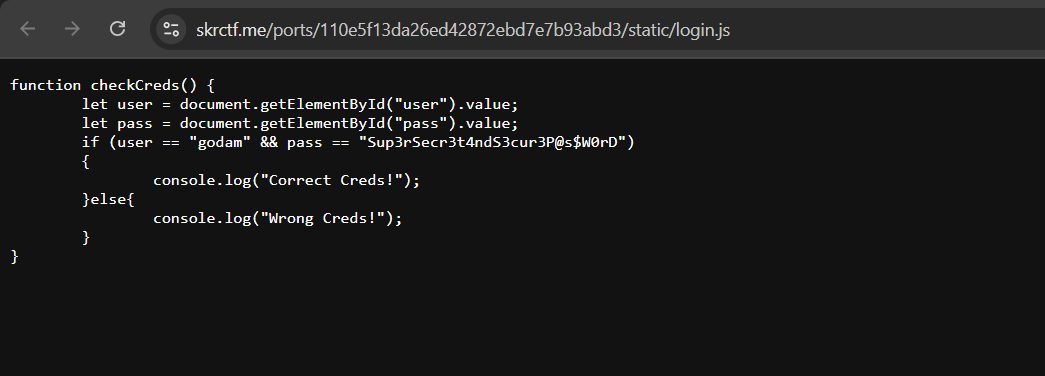
Step 3: I checked the sources and found a file named as "static/login.js" and opening this file, I found the following code:
function checkCreds() {
let user = document.getElementById("user").value;
let pass = document.getElementById("pass").value;
if (user == "godam" && pass == "Sup3rSecr3t4ndS3cur3P@s$W0rD") {
console.log("Correct Creds!");
} else {
console.log("Wrong Creds!");
}
}
|
Step 4: The credentials were literally hardcoded into the JavaScript on the client side. I used:
Username: godam
Password: Sup3rSecr3t4ndS3cur3P@s$W0rD
|
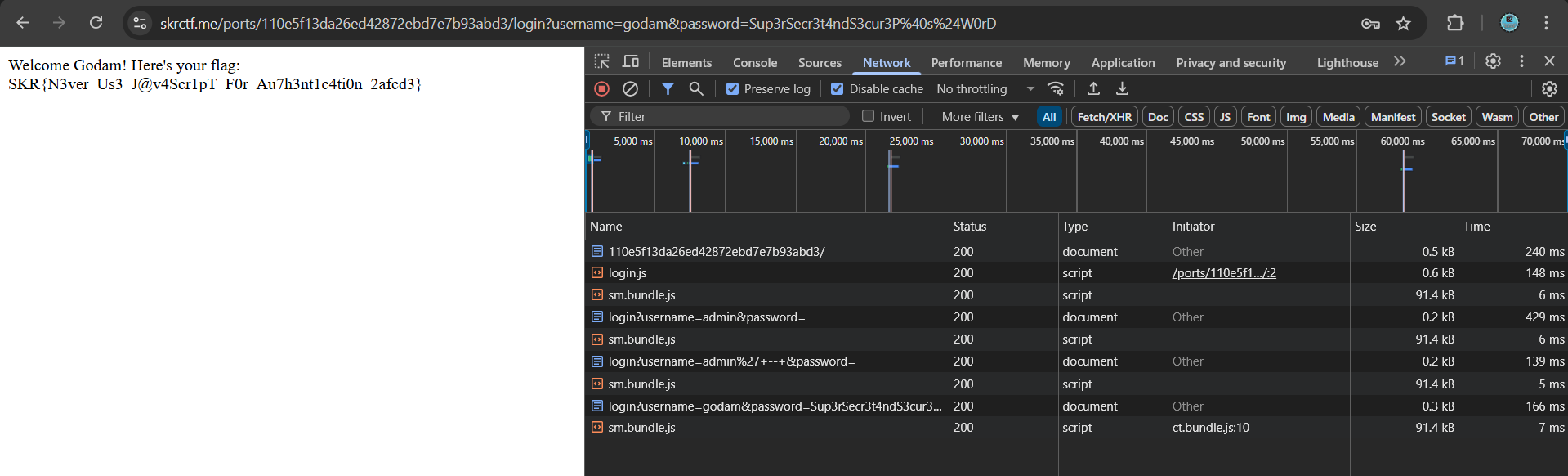
Step 5: Upon entering the correct credentials, the site responded with:
Welcome Godam! Here's your flag: SKR{N3ver_Us3_J@v4Scr1pT_F0r_Au7h3nt1c4ti0n_2afcd3}
|
This challenge served as a straightforward reminder of a critical security best practice: never implement authentication solely on the client side. By exposing credentials in JavaScript, the developers unknowingly allowed attackers to bypass the login system entirely. While this was a beginner-friendly CTF task, it reflects real-world vulnerabilities that can have serious consequences if overlooked. Always ensure authentication is securely handled on the server, and avoid exposing sensitive data in client-side code.