Category: Cyber Security (CYB)
Browse all posts in this category

Vulnerability Report: Unauthenticated RTMP Push & Public Playback on Kuaishou (快手短视频)
A critical vulnerability has been discovered in the Kuaishou streaming infrastructure that allows unauthenticated live streaming via RTMP to arbitrary stream keys. Once pushed, these streams are publi...
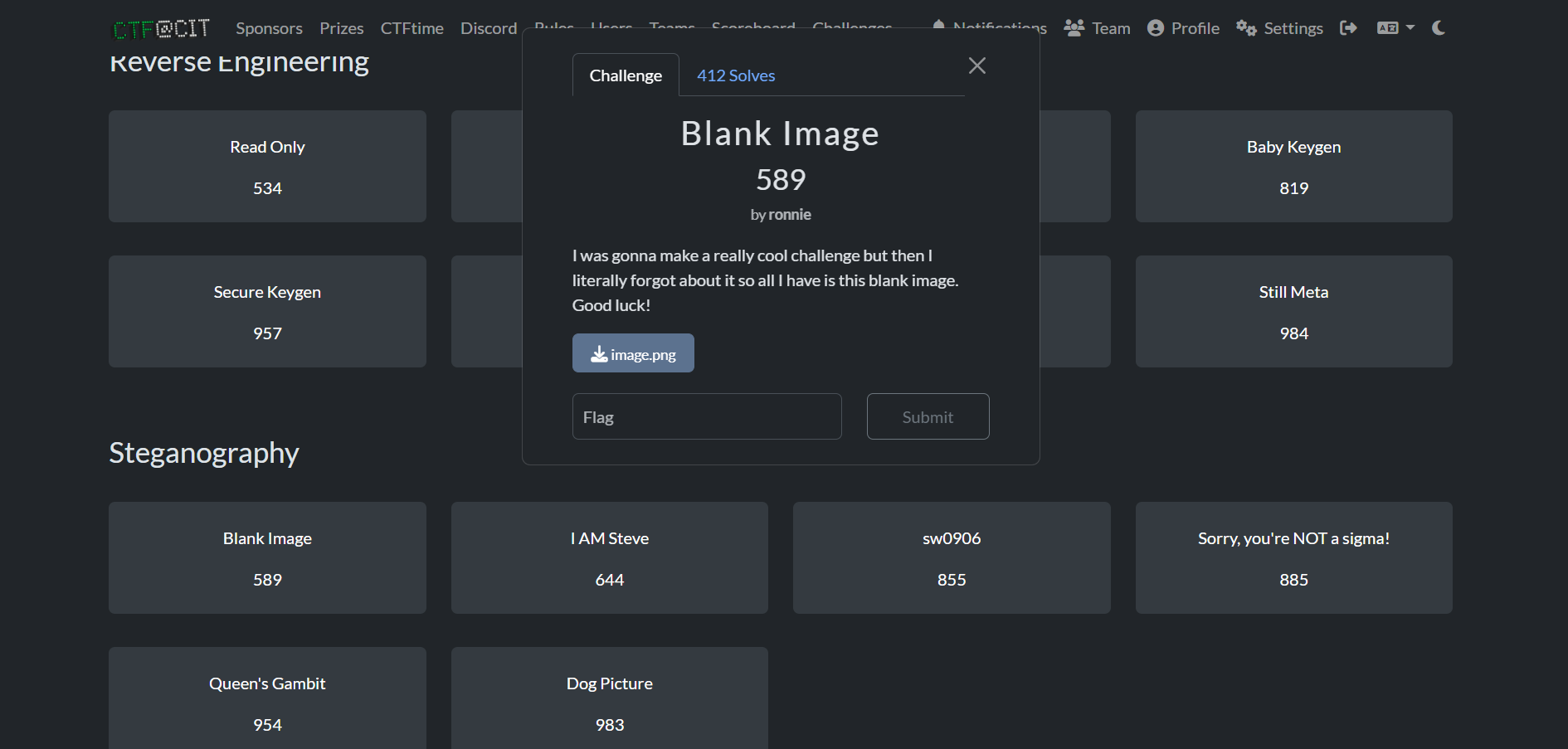
CTF@CIT 2025 Write-Up: Blank Image (Steganography)
In the CTF@CIT 2025 cybersecurity competition, I participated in the Steganography category and came across an interesting challenge named "Blank Image". Despite appearing as a blank image, a clue in ...

CTF@CIT 2025 Write-up: Breaking Authentication via SQL Injection
In this challenge, we are presented with a seemingly innocent login form and a mysterious prompt: "Say my username." While it appears simple on the surface, this challenge requires a solid understandi...
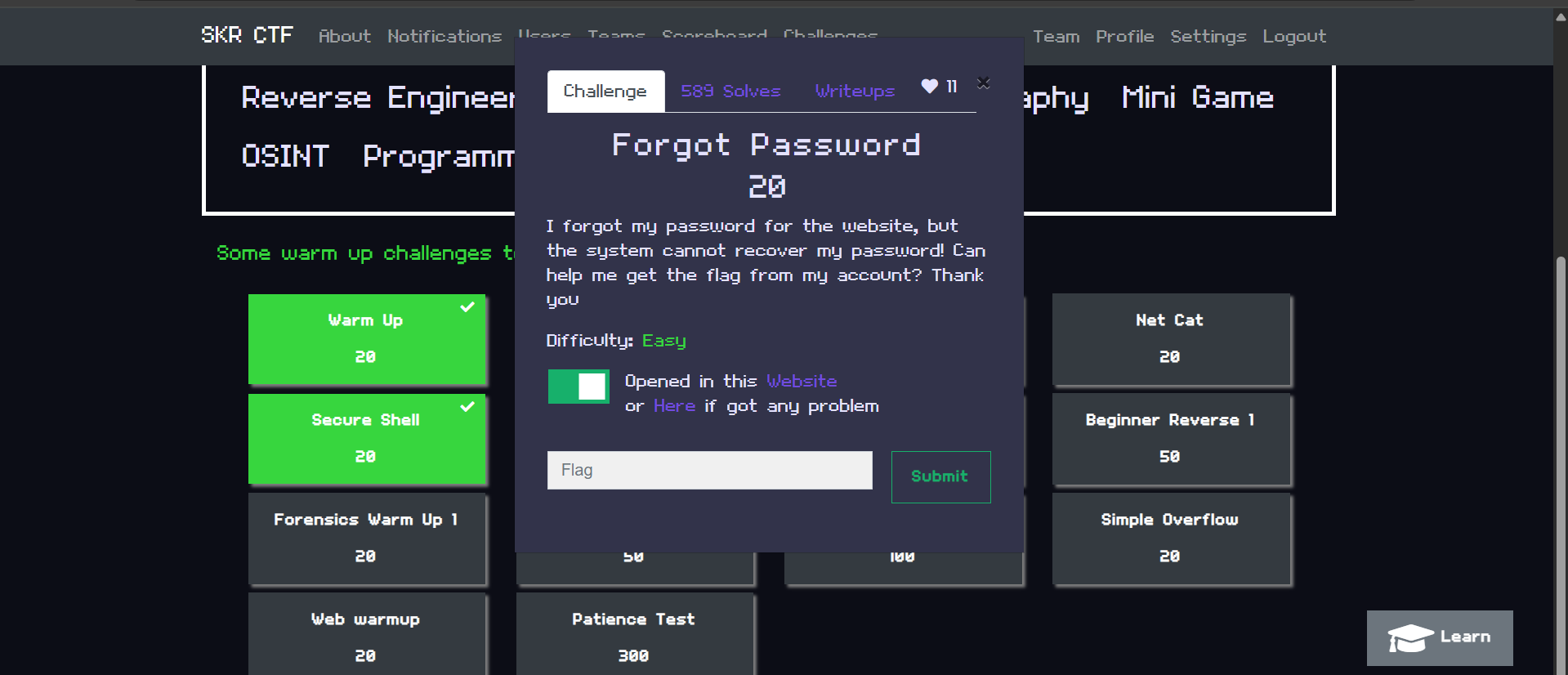
SKRCTF - Forgot Password Challenge: Exploiting Client-Side Authentication
The "Forgot Password" challenge from SKRCTF highlights a classic web security flaw commonly seen in beginner-level Capture The Flag (CTF) competitions. The challenge presents a simple login page where...
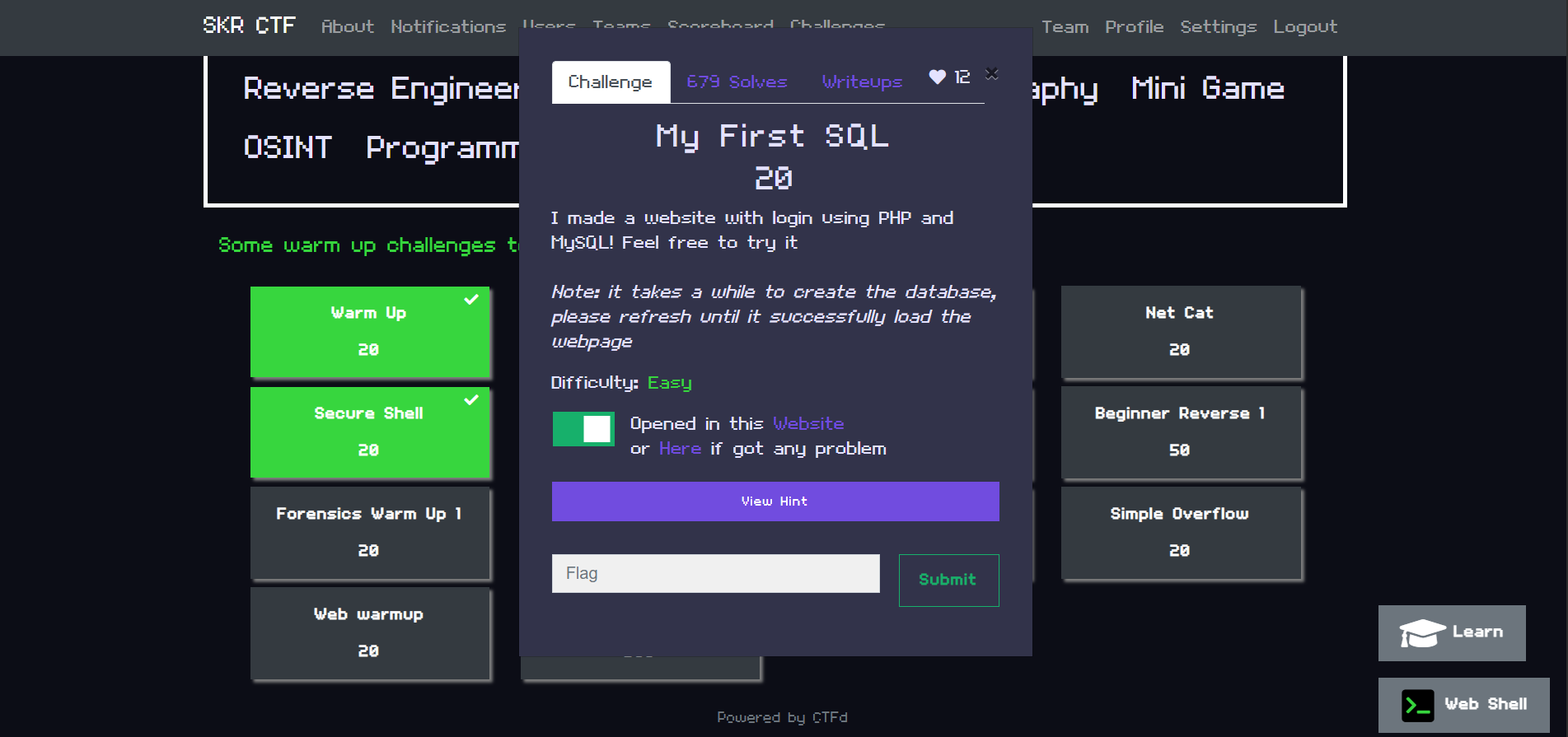
SKRCTF: My First SQL – Beginner SQL Injection Challenge Writeup
The "My First SQL" challenge from the SKRCTF series offers an accessible introduction to SQL injection (SQLi) vulnerabilities, making it an excellent starting point for individuals new to web security...
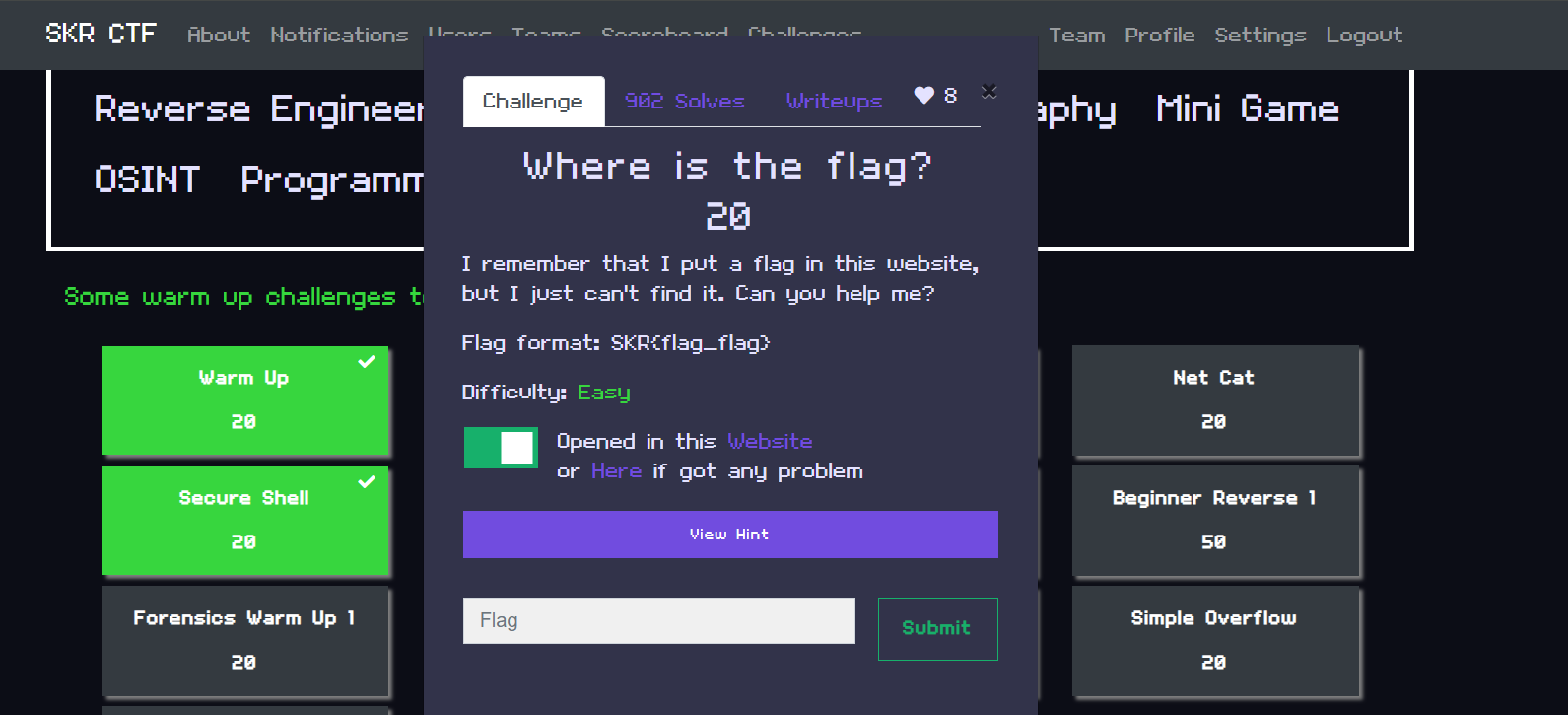
SKRCTF: Where is the Flag? – Web CTF Challenge Writeup
The "Where is the flag?" challenge from the SKRCTF series is a beginner-friendly web challenge that emphasises the importance of thorough inspection and attention to detail in web security.Challenge O...
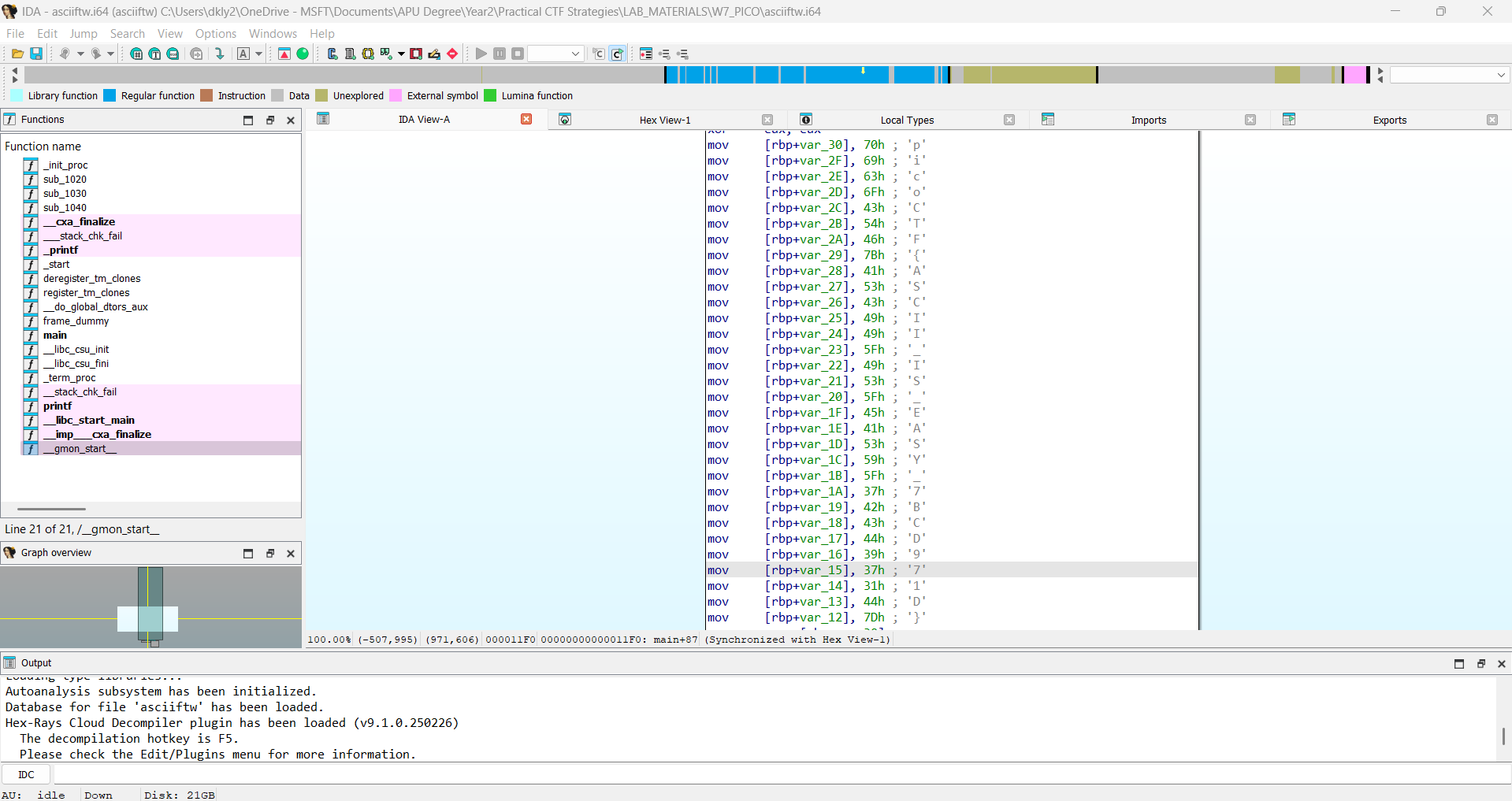
Reverse Engineering in picoCTF: A Journey Through Binaries, Bits, and Flags
Reverse engineering is a core skill in cybersecurity that involves analyzing a system, software, or binary to understand its design, functionality, or hidden components, often without access to its so...
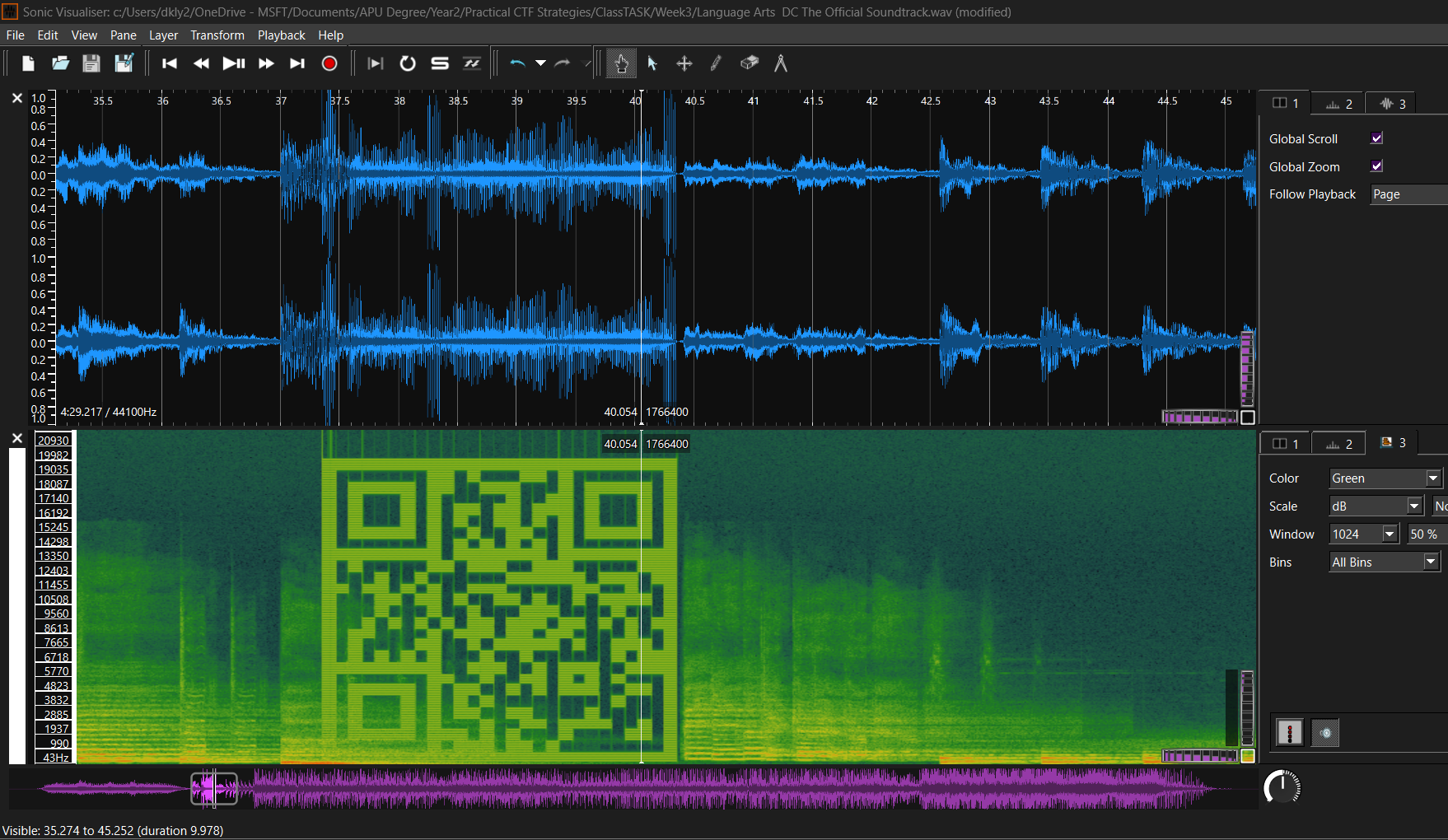
CTF Audio Steganography: Hands-On Strategies for Decoding Hidden Messages
In this class task, you will explore the fascinating field of Audio Steganography, where information is hidden within audio signals. Through a series of tasks in Part A and Part B, you will utilize sp...